The Ideal IT Architecture
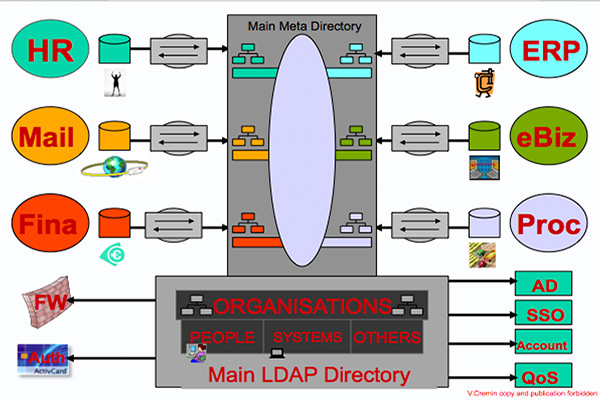
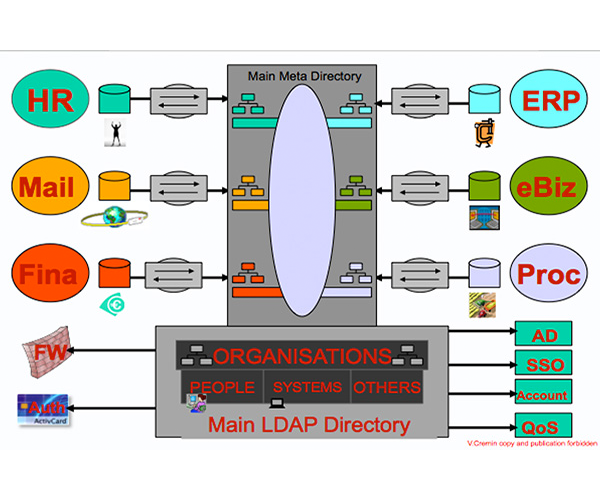
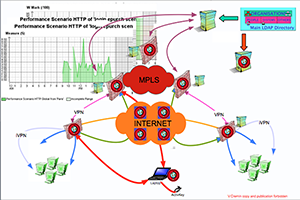
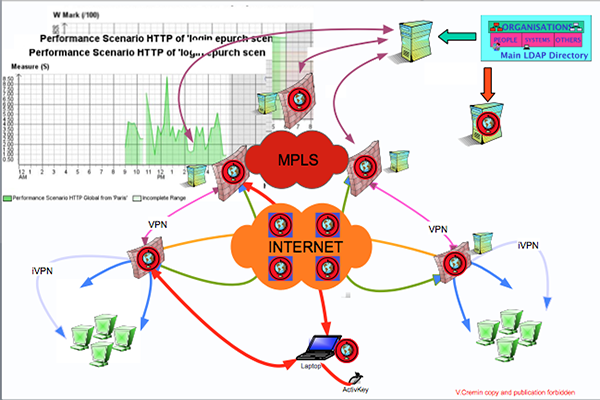
The very first and Basic component of an architecture is the Directory. The information shared between several application is stored in a structured and standardised format: the DIT (Directory Information Tree). Because of its performance in terms of the access time (using LDAP) and replication between servers , but also because of its imbedded level of security and object architecture it is the only technology able to offer a consistent and efficient image of the company supplied to all the business , web, security ‚?¶ applications.
This is especially fundamental for a security architecture which checks permanently user's identities, profiles and object's characteristics. The directory is the container of the authorised employee and company information, including: organisations, credentials, passwords, certificates, tokens and complemented by a set of legalised data coming from HR, Mail , Business, Finance .. applications.
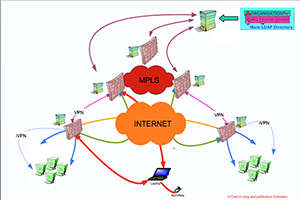
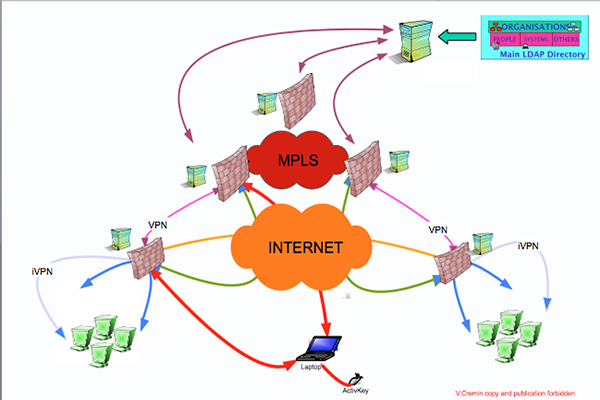
The directory distributes these information to all the IS architecture components but specially to FWs, Authentication Systems, Accounting Systems, QoS components. The information managed by the Directory is automatically updated by a MetaDirectory connected to the HR, Mail, Finance ... systems.
The MetaDirectory synchronises all the heterogeneous data sources between them : SQL Bases, Mail Address Books, SAM bases , Active Directory and any other format of storage.
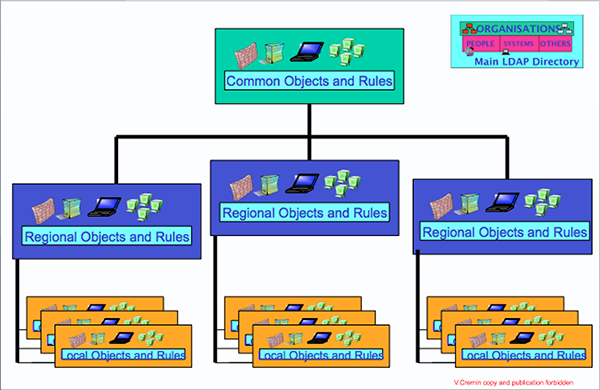
The flow engine of the MetaDirectory, programmed with appropriate rules, is able to determine who is the owner of each information to be legally distributed to the others. This tool guarantees the consistent view and automatic update, from a unique source, of the whole Information System. The DIT is populated by the MetaDirectory and it is the most efficient container to be used by all the LDAP enabled applications.
MY CONTRIBUTION as Project Manager and Architect
1- The Security Policy: Top-Down approach based on ISO 17799
a) Design of The Policy based on ISO 17799, adapted to business requirements
b) High Management support
c) Implementation of a light security organisation in all the countries
d) Organisation of the census and roadmaps to reach the policy
e) Audit of sites and update of the Policy
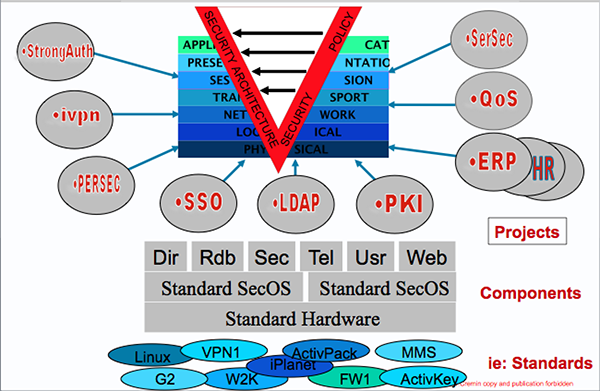
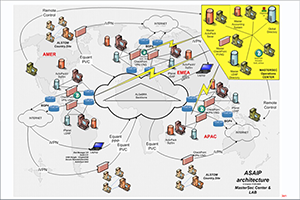
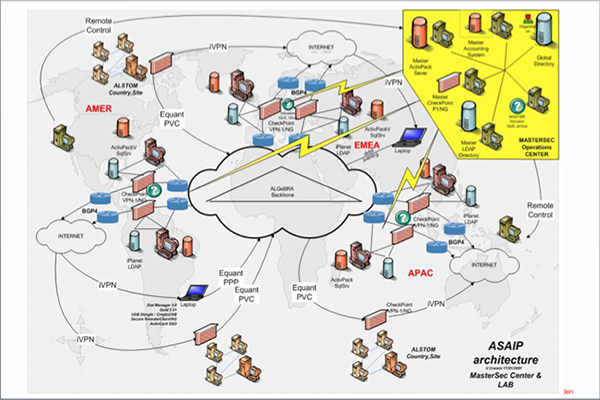
2- The Security Architecture: Bottom-up approach based on best practices
a) Choice of a limited but consistent number of technologies and products
b) Adaptation of products to Interoperate in a common Architecture
c) Design of Standard Components based on products but with a specific setup
d) Design of projects based on standard components to reach policy requirements
To the Top






 About THIS Website
About THIS Website  "
The Community is the best , the only way. No developments , no Architectures and even the required Security level can be reached without the community
"
The Community is the best , the only way. No developments , no Architectures and even the required Security level can be reached without the community Using last technologies , shared resources, and the community , is becoming easy and cheap to build even sophisticated architectures, to have the very last parent of MalWare , to be quickly informed and even alarmed about new availabilities , new needs.
Using last technologies , shared resources, and the community , is becoming easy and cheap to build even sophisticated architectures, to have the very last parent of MalWare , to be quickly informed and even alarmed about new availabilities , new needs. 



